How to Write an Effective IAM Policy
The identity access and management (IAM) concept is very commonly used in AWS services when dealing with security, so it’s well worth understanding it in more detail. IAM can seem very complicated for the first-time user because it consists of different components. The purpose of this article is to explore IAM and its concepts in more detail and to create an effective IAM policy.
It’s important to remember that IAM is just another service like all the other ones that AWS has to offer. However, it serves to bring them together in a safe manner.
What is an IAM Policy?
AWS IAM is a web service that enables you to securely manage your users' access to S3 resources. You use IAM to manage who can access your AWS resources (authentication), what resources they can access, and how they can access them (authorization).
How Does IAM Keep Resources Secure?
You control access to resources by setting rules and associating them with IAM identities (users, groups of users, or roles). A policy is an object that specifies the permissions associated with an identity or resource. The greater storage system examines these rules when an IAM principal (user or role) submits a request in order to effectively implement them. Permissions defined in policies dictate whether a request is permitted or denied. Most policies are JSON files.
IAM rules establish authorization for actions independent of how the activity is performed. If a policy permits the GetUser action, a user with that policy may get user information through the AWS Management Console, the AWS CLI, or the AWS API. When creating an IAM user, you can specify whether console or programmatic access is permitted. If console access is allowed, the IAM user may log in using their username and password. Alternatively, if programmatic access is allowed, the user may work with the CLI or API using access keys.
How Do IAM Policies Optimize Seagate Lyve Cloud Storage?
Lyve Cloud serves as a complimentary element to S3 object storage. Seagate Lyve Cloud adds security and usability to long-term cold storage and can be partnered with additional services to enhance backup and recovery protection. Use IAM policies to customize security measures and permissions for individual objects stored within Lyve Cloud across private, public, hybrid, and multicloud environments.
IAM Policy Types
The following policies are available in AWS from most used to least frequently used. For further information on each policy category, check the sections below.
Identity-based policies
You can connect IAM identities to controlled and inline policies (users, groups to which users belong, or roles). Permissions are granted to identity via identity-based policies.
Resource-based policies
You can connect resources to inline policies. The most frequent resource-based policies are those associated with S3 buckets and IAM roles. Permissions are granted to the principal defined in the policy via resource-based policies. Principals might be in the same or different accounts as the resource.
Permissions boundaries
You can utilize a managed policy to define the permissions for an IAM entity (user or role). This policy establishes the maximum permissions that identity-based policies may provide an entity but does not issue them. Permissions boundaries do not specify the maximum number of permissions that a resource-based policy may issue an object.
Organizations SCPs
You can utilize an AWS Organizations service control policy (SCP) to set the maximum permissions that an organization or organizational unit's account members may have. SCPs limit the rights that identity-based or resource-based rules provide to account entities (users or roles) but do not grant them.
Access control lists (ACLs)
You can use ACLs to restrict access to a resource by principals in other accounts. ACLs are similar to resource-based policies; however, they are the only form of policy that does not employ the JSON structure for policy documents. ACLs are permissions rules that span several accounts and provide permissions to the specified principal. ACLs cannot be used to give permissions to entities that are members of the same account.
Session policies
You may pass advanced session rules when you use the AWS CLI or AWS API to assume a role or a federated user. Session policies restrict the rights granted to the session by the role or user's identity-based rules. These policies define the permissions associated with a newly established session but do not grant them.
Important Elements in the Structure of IAM Policy
IAM user
AWS IAM users are entities you create to represent any person or application that interacts with AWS. AWS users consist of a name and credentials.
IAM users with administrator permissions are not the same as AWS account root users. AWS accounts are associated with one and only one IAM user.
IAM identity
Resource objects that are used to identify and group IAM resources. Policies can be attached to IAM identities. This includes users, groups, and roles.
IAM resource
It contains objects such as users, groups, roles, policies, and identity providers. IAM allows you to add, edit, and remove resources like other AWS services.
IAM entity
AWS uses IAM resource objects for authentication. Among these are IAM users and roles.
Principal
An application or user that uses the root user of the AWS account, an IAM user, or an IAM role to sign into AWS. This includes federated users as well as assumed roles.
Role
In AWS, roles are similar to users since they are identity objects whose permission policies determine what the identity can do. However, a role is not associated with any credentials (passwords or access keys). An individual role is intended to be assumed by anyone who needs it, rather than being associated with only one individual.
How to Write an Effective IAM Policy
You may build a customer-managed policy using one of the following techniques in the AWS Management Console:
- JSON: Paste and modify an example identity-based policy that has been published.
- Visual editor: Use the visual editor to create a new policy from scratch. You do not need to learn JSON syntax if you utilize the visual editor.
- Import: From inside your account, import and modify a managed policy. You may import a previously developed AWS managed policy or a customer-managed policy.
AWS accounts have a restriction on the number and quantity of IAM resources. More information is available at IAM and AWS STS quotas.
IAM Policy Generator: Can I Automate This Process?
The AWS Policy Generator is a tool for developing rules that govern access to AWS products and resources.
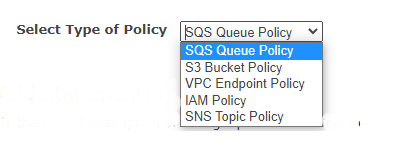
The newly released AWS Policy Generator streamlines the process of developing policy documents for object storage purposes. To begin, choose the type of policy you want to write.
Step 1: Select Policy Type
Permissions are included inside a policy. You may construct the following kinds of policies: IAM Policies, S3 Bucket Policies, SNS Topic Policies, VPC Endpoint Policies, and SQS Queue Policies.
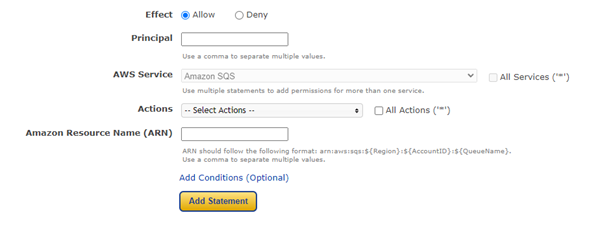
Step 2: Add Statement(s)
A statement is a concise overview of a single permission. Check out the following explanation of the items that may be used in statements.
Step 3: Generate Policy
After adding statements, you can generate a policy. A policy is a document (in the Access Policy Language) that contains one or more statements.